“Phishing emails are bait emails that cyber criminals usually sends to a large set of recipients whose emails they’ve mined on the internet.”
Their goal is to lure you into their bait, which may be presented as: an unmissable opportunity for you, massive discounts, claiming of your winnings, etc.
They normally catch your blind spot, which may be a weakness that you’re undergoing at that stage of your life, i.e. your urgent need for capital.
They send these phishing emails en-masse, and wait for their target to bait!
These emails are increasingly making their way into our spam folders as cyber criminals become ever more creative at catching our blind spots.
They often use countless techniques to bait you, and some are blatantly obvious, whilst others are not.
The most important thing to remember is to be as relaxed as possible and do the necessary vetting of the sender.
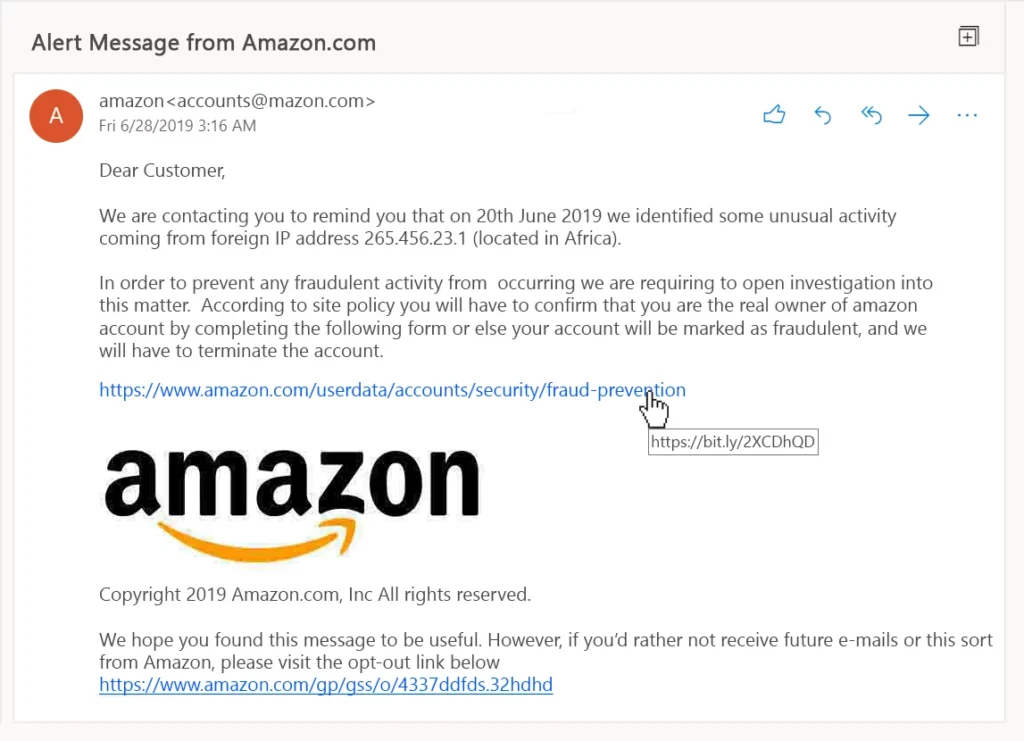
Remember, there is no stranger that has your best interest at heart, and wants to reward you with unrealistic gifts and money out of love!
Below are some of the most common red-flags to watch out for as of this year!
-
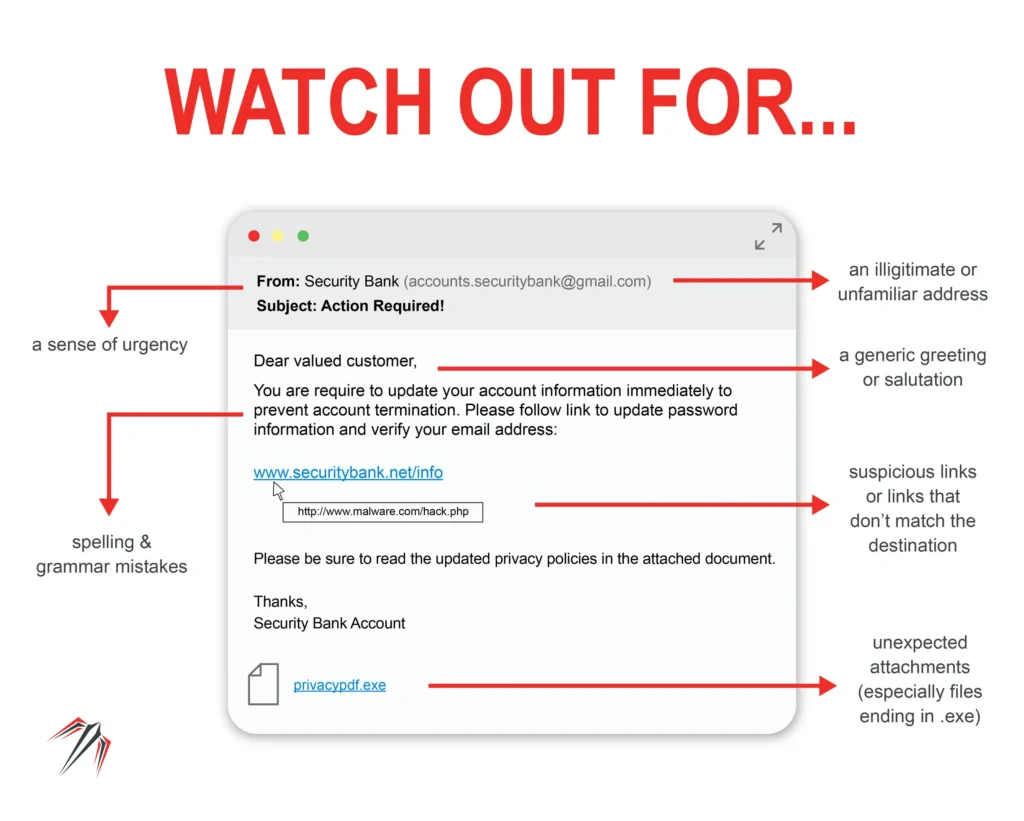
Poor spelling and formatting. Scammers normally fail to write formal emails that make sense or are associated with a business they and yourself have in common. Rather they want to swindle your emotions by causing panic. Meanwhile, their content is irrelevant to you.
-
Domain. They normally use @gmail | @yahoomail | @outlook, or any other generic domain that is easy to set up and get going with. Always check the sender. Verify their domain by comparing it to their organization, e.g. person@organization.com! This is important!
-
Broken images. Their images are normally broken, which is a red-flag. Broken images do not show the image. This could be their way of bypassing the spam filter. Be on the lookout!
-
Concealed URLs. They use concealed URLs that will redirect you to a malicious site where they can extort your data off of you! To prevent this, always hover over their link to disclose the underlying URL. You will quickly notice that something is phishy here.
-
Attachments. As with point number four, they normally attach documents that they wish to bait you with. Only open these if you are expecting them, know what they are or have verified the sender.
-
Long-winded emails. Scammers normally use long-winded emails that quickly become nonsensical. If the email comes from a reputable company, then their email will always be concise.
-
Nuanced emails. Sometimes scammers will create emails that come close to legitimate as possible. However, they aren’t. Here’s an example: queries@googlee.com. (Notice the extra ‘e’)
-
Nuanced website URLs. Same as above, point 7.
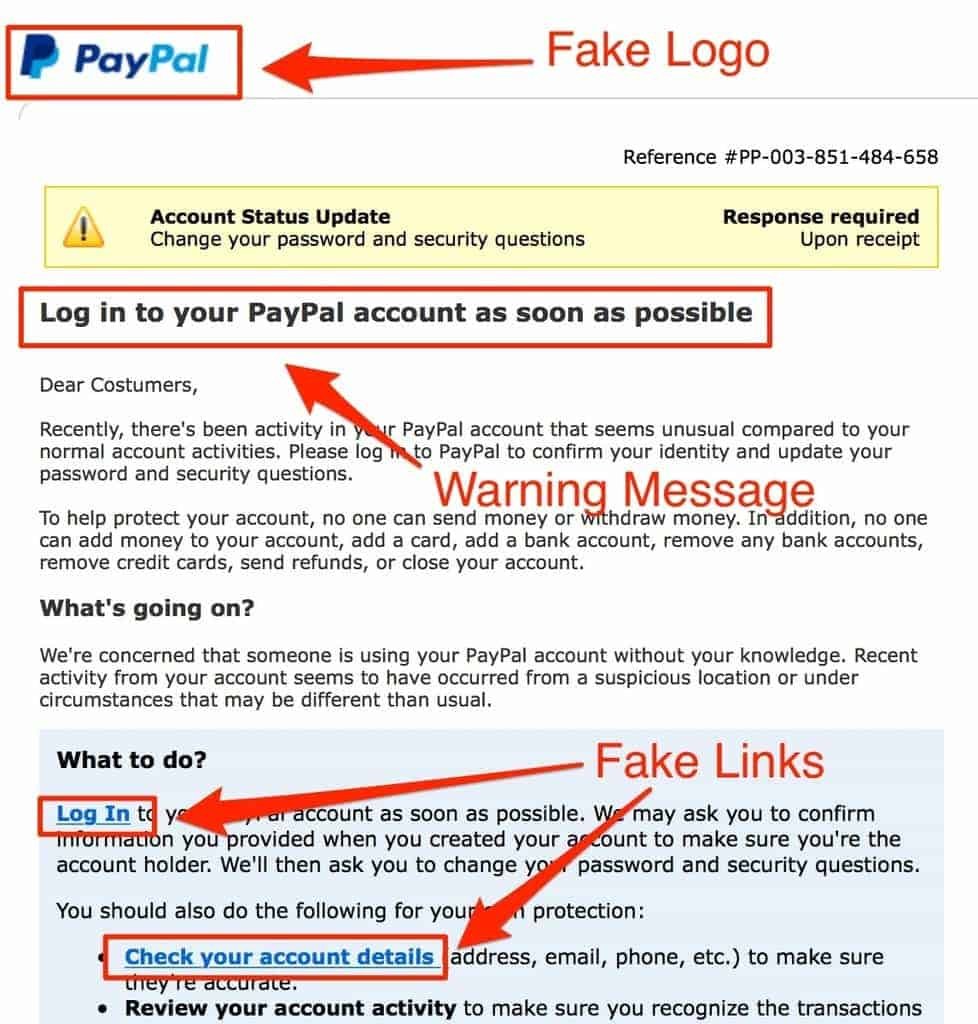
Sometimes they get the right domain, and it’s hard to tell why. For instance, I received an email from forms@google.com that said that I had 2bitcoins that were ready for my collection. This was baffling to me as to how these phishers managed to infiltrate a Google domain. However, as per what I mentioned above, I calmed and remembered that no one was gracious enough to give me 2 Bitcoins out of generosity. Everyone needs capital, and people seldom give it away, least of all hundreds of thousands worth of it. TO STRANGERS!
-
Sense of urgency. Scammers will often use urgent words to stir panic in you and then scam you out of your earnings. THEY ALWAYS DO THIS.
Be on the lookout, and you are largely free from these pests! Thanks!
Go back here!
You may also like my post on how to self-publish a book on Amazon! This is a very slight update to my earlier post on the same subject, check: How to spot email phishing.



